Continue,
In the previous article, I already define the advantages and references that can be used for Change Management process, in this article it will focusing on what the important parameters used to ensure enablement and supporting Change Management to be applied in your enterprise.
Service Catalogue
As the baby step to build Change Management process is build a service catalog of your enterprise. What is Service Catalogue? Refer to ITIL, service catalogue is a database or structured document with information about all live IT services, including those available for deployment. The service catalogue is part of the service portfolio and contains information about two types of IT service: customer-facing services that are visible to the business; and supporting services required by the service provider to deliver customer-facing services. As reflection question is do you know what kind of IT services which available in your enterprise? Ask the same questions to your co-workers, do they answer same as yours? If there any differences, than you should start to gather all the scattered information and verify every answers too ensure all internal personnel have an identical view.
What kind the information should include in service catalogue? Here they are:
Change Management Database (CMDB)
The next part is Change Management Database (CMDB). Refer to ITIL, CMDB is database used to store configuration records throughout their lifecycle. The configuration management system maintains one or more configuration management databases, and each database stores attributes of
configuration items, and relationships with other configuration items. Simply, CMDB have a role to maintain all changes which implemented in the IT Services reflect to service catalogue.
This is also not a day job. It need a dedicated person / team to maintain the accuracy of CMDB. Through this we can view and review all changes which implemented in the enterprise. If there's a incident caused services disruption, then CMDB become an essential part for the enterprise, especially for IT personnel to view what kind of changes yet implemented. It will create an awareness for personnel to conduct comprehensive development, analysis and approval before they perform the changes in the services.
The essential part in CMDB is Configuration Item (CI). Definition of CI is service asset that
needs to be managed in order to deliver an IT service. Examples of configuration items are a server or a software licence. The CMDB will mapping the service catalogue to CI. So, it will bring an advantages for the personnel to completely view structure of the services.
To ensure the CIs accurately better to using automate solution which provide by various vendors. It will collect all data inside the CIs. It need an agent to be injected in CIs to completely gather all the information. Some of elements that will need to be gather such as:
That's it for today, it will continue in next article.
Thank you for reading.
- EJ
In the previous article, I already define the advantages and references that can be used for Change Management process, in this article it will focusing on what the important parameters used to ensure enablement and supporting Change Management to be applied in your enterprise.
Service Catalogue
As the baby step to build Change Management process is build a service catalog of your enterprise. What is Service Catalogue? Refer to ITIL, service catalogue is a database or structured document with information about all live IT services, including those available for deployment. The service catalogue is part of the service portfolio and contains information about two types of IT service: customer-facing services that are visible to the business; and supporting services required by the service provider to deliver customer-facing services. As reflection question is do you know what kind of IT services which available in your enterprise? Ask the same questions to your co-workers, do they answer same as yours? If there any differences, than you should start to gather all the scattered information and verify every answers too ensure all internal personnel have an identical view.
What kind the information should include in service catalogue? Here they are:
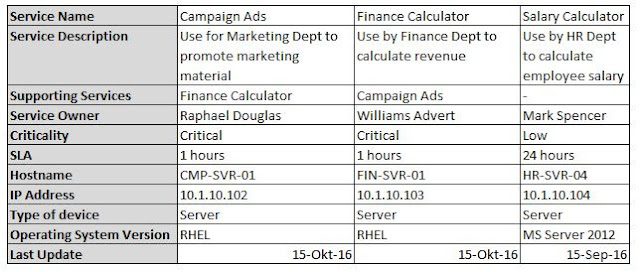
- Service Name, referred to services which known to users / IT personnel.
- Service Description, used to additional information related to service name.
- Supporting Services, used to describe which services supported this services.
- Service Owner, define owner (person in the enterprise) of the services.
- Criticality, define level of service criticality to the enterprise business.
- Service Level Agreement (SLA), related to expectation of availability of services.
Change Management Database (CMDB)
The next part is Change Management Database (CMDB). Refer to ITIL, CMDB is database used to store configuration records throughout their lifecycle. The configuration management system maintains one or more configuration management databases, and each database stores attributes of
configuration items, and relationships with other configuration items. Simply, CMDB have a role to maintain all changes which implemented in the IT Services reflect to service catalogue.
This is also not a day job. It need a dedicated person / team to maintain the accuracy of CMDB. Through this we can view and review all changes which implemented in the enterprise. If there's a incident caused services disruption, then CMDB become an essential part for the enterprise, especially for IT personnel to view what kind of changes yet implemented. It will create an awareness for personnel to conduct comprehensive development, analysis and approval before they perform the changes in the services.
The essential part in CMDB is Configuration Item (CI). Definition of CI is service asset that
needs to be managed in order to deliver an IT service. Examples of configuration items are a server or a software licence. The CMDB will mapping the service catalogue to CI. So, it will bring an advantages for the personnel to completely view structure of the services.
To ensure the CIs accurately better to using automate solution which provide by various vendors. It will collect all data inside the CIs. It need an agent to be injected in CIs to completely gather all the information. Some of elements that will need to be gather such as:
- Hostname
- IP Address
- Type of devices: servers, network device, security devices, etc
- Software / Operating System version
- Etc
Example of Simple CMDB
That's it for today, it will continue in next article.
Thank you for reading.
- EJ